March 26, 1999
More than 100 U.S. corporations were hit.
Comments inside the macro virus identify it as "Melissa...by Kwyjibo." Watch for Subject in Email "Important Message From " and contains the sentence: "Here is that document you asked for...don't show anyone else ;-)." the attachment is usually called list.doc. If there is an Atachment = Paperclip Grafic or a File usually at the bottom of the Email DELETE it imediatly Melissa is the Word97/Word 2000 macro virus that peeks into a user's Outlook address book, steals up to 50 addresses and sends copies of its host documents out without the user's knowledge. The original and most common document contains a list of Triple-X sites on the World Wide Web. However, the virus can infect any Word 97/Word 2000 document including those containing sensitive information, Melissa mutates After the virus began circulating around the Internet on Friday, IT managers worked furiously to block its spread, filtering out e-mails with the original subject line. But now they'll need to go back to the drawing board because the new variants could bypass protections already put in place. Already, a variant with a blank subject line has emerged on the Internet, according to Trend Micro Inc. Another one, using an Excel macro to spread was posted on the news group alt.bondage and is contained in a message labeled "Urgent info inside. Disregard macro warnings." While the new variants complicate the prescription for network health, the most effective fix still remains the simplest: Don't open a macro in an e-mail attachment. A poster called "Sky Roket" launched the Melissa virus into the wilds via the newsgroup alt.sex early Friday morning. antivirus company Network Associates said today. March 29, 1999 Electronic mail traffic was disrupted at businesses throughout the country Friday as mail systems were overloaded by a computer virus, dubbed Melissa by its creator, that spreads itself at lightning speed. The extent of the disruptions is unclear, but companies ranging from Microsoft Corp. to Intel Corp. said they had been infected. Employees at major banks and several smaller companies said they had been affected and in some cases had their mail systems shut down during parts of the day. Although it spreads rapidly, overloading e-mail networks, the virus is not known to cause serious harm, such as deleting files or scrambling information on hard disks. By the end of the day, all major makers of anti-virus software had tools to squash the virus available on their Web sites. ``We believe that there are tens of thousands of people being infected already,'' said Sal Viveros, a marketing manager at security software maker Network Associates Inc. ``It is one of the fastest-spreading viruses that we have seen.'' Viveros said the company had received more than 100 notices from customers saying they had been infected. Home e-mail users could be infected and may receive a flood of unexpected messages that could overload their Internet service provider's system. The virus is transmitted through Microsoft Word 97 attachments to e-mail messages. Once a user activates the virus by opening the attachment, the virus culls up to 50 names from the user's electronic address book and sends itself automatically to those other users. The virus typically arrives in an email headed: ``Important Message From .'' The text of the email reads ``Here is a document you asked for. . . don't show to anyone else ;-)'' Once a user opens it, the attachment contains a list of pornographic Web sites. By then, damage is done, and the e-mail will have replicated itself to up to 50 other users. The virus has one additional side effect: If a user downloads the virus when the minute reading of the current time matches the date of the month -- for example, at 8:26 p.m. on March 26 -- the virus inserts the following quote from cartoon character Bart Simpson in the users document: ``Twenty-two points, plus triple-word-score, plus fifty points for using all my letters. Game's over. I'm outta here.'' Users can avoid spreading the virus by simply refusing to open the e-mail attachment.
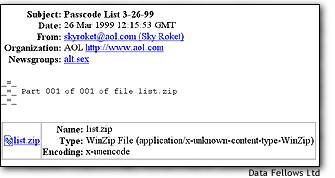
Melissa virus launch identified March 29, 1999 After Network Associates heard about Melissa from a customer, its newsgroup-sniffing software was able to track down the point at which the virus first emerged, Viveros said. The company knows it was the first insertion into the world because the original file, "list.doc," had a creation date just a bit younger than the time it was inserted. Network Associates looked at the sex-related newsgroups because of the pornographic content of the "list.doc" file originally used to spread the Melissa virus, Viveros said. The file was initially posted at 4:15 a.m. Pacific time on Friday, he said. Sky Roket apparently has posted as far back as 1997 to other sex-related newsgroups with virus-infected files named things like "complete list of adult sites" and "complete list of cracked Web sites." The Melissa virus spreads using a combination of Microsoft Outlook and Microsoft Word. Major antivirus companies posted updates for their virus-checkers on their Web sites. However, experts cautioned that the characteristics of the virus are changing as programmers modify the Melissa programming instructions for their own viruses. "This is the fastest-spreading virus we've ever seen," (Name) said. "It's all over the world--Asia, Europe, South Africa, New Zealand, Holland." Antivirus company Symantec said the speed of the Melissa propagation caught antivirus makers "off guard." While (Name) took issue with the statement, saying that Network Associates had its update available less than three hours after the company first heard of the virus, its software didn't protect against Melissa until that update was installed. Several of Network Associates' antivirus clients were infected with Melissa, including one site that had 60,000 users infected on Friday and other that had more than half a million infected emails in its system, Viveros said. "The writer was very clever," (Name) said. "This one is spreading rapidly because it's coming from a trusted source. Most of the other viruses use very generic text where it's easy to identify it's not from a trusted source. They don't spread as quickly." Melissa takes advantage of mailing lists in Outlook. One of the characteristics of the virus-writing community is that authors quickly adopt innovations. Indeed, Melissa.a, similar to Melissa but with a blank subject line, has been circulating. Papa is similar, though it uses Microsoft Excel instead of Word to propagate, but (Name) said it's relatively toothless because the author "broke" the replication code so it doesn't spread as effectively as Melissa. The quick-change nature of some viruses make them similar in some way to the human immodeficiency virus (HIV), the virus that causes AIDS. HIV's rapid mutation rate enables it to evade new detection and treatment technologies. However, (Name) said he was confident Network Associates' software will be able to catch future variants of Melissa. Though Melissa won't fully work on Windows computers without Outlook or on Macintoshes, the virus still can lie dormant on those machines if a user opens up a Melissa-infected Word file, (Name) said. In that scenario, Melissa would infect the computer and the template file Word uses to create new documents. If a new Word document then were sent to Windows user who did have Outlook and Word, a new round of Melissa mailings could result. And this time, the file it would piggyback on would be the new Word file instead of Melissa's original list of porn sites. That could be bad if the new Word document were a payroll list, for example.
National Infrastructure Protection Center Computer Virus Alert: Word/Melissa (aka W97/Melissa) Macro Virus The National Infrastructure Protection Center (NIPC) was notified on March 26, 1999, of the proliferation of a computer virus known as the "Melissa Macro Virus" (MMV). There have been widespread reports of propagation of this virus into commercial, government and military e-mail gateways and systems. The MMV has the capability of causing a denial of service and degraded computer network performance, which could result in system administratorsí having to shut-down affected networks and e-mail servers. The NIPC has received reports of significant network degradation and e-mail outages at major corporations and Internet Service Providers. The NIPC has received no reports of the virus causing any alteration of or damage to any data contained in the infected systems. The MMV exploits a vulnerability that exists in the Microsoft computer software applications Word 97 and Word 2000. The virus is transmitted via an attachment to innocuous e-mail messages transmitted to unsuspecting computer users via the Internet and related networks. The virus is activated when a user opens the infected document. A command is immediately executed that lowers the security settings in the Microsoft Word 97 or Word 2000 application to permit all macro files to run and any newly created Word documents to be infected. The virus spreads by transmitting e-mail messages containing the infected documents to addresses contained in the infected user's e-mail address book. Corrective measures have been developed to guard against infection by the "Melissa Macro Virus" at the network and user level. In addition, leading virus detection utilities (including Symantec{http://www.symantec.com}, McAfee {http://www.mcafee.com}, and Trend Micro {http://www.antivirus.com}), when updated properly after March 26, 1999, reportedly detect and clean this type of macro viruses. NIPC Director (Name) states, "e-mail users have the ability to significantly change the outcome of this incident. I urge e-mail users to exercise caution when reading their e-mail for the next few days and to bring unusual messages to the attention of their system administrator. The transmission of a virus can be a criminal matter, and the FBI is investigating." The MMV has significant potential to cause more-widespread harm than it has to date. In an effort to reduce the impact of the MMV on computer networks, users can take several actions: As the virus requires the user to open an infected document to continue the propagation, users should carefully check their e-mail boxes for any message containing as part of the subject: Important Message From If such a message is found, please contact your system administrator or other responsible party for assistance. Users and system administrators alike should consult reputable information sources for more assistance on how to detect and minimize the impact of the MMV. Information on detection and mitigation strategies can be obtained online from CERT® (the Computer Emergency Response Team at Carnegie Mellon University) at http://www.cert.org. The NIPC is a multi-agency organization whose mission is both a national security and law enforcement effort to detect, deter, assess, warn of, respond to, and investigate computer intrusions and other unlawful acts that threaten or target our Nationís critical infrastructures. Located in the FBI's headquarters building in Washington, D.C., the NIPC brings together representatives from the FBI, other U.S. government agencies, state and local governments, and the private sector in a partnership to protect our Nation's critical infrastructures.
Melissa virus "originator" bewildered March 30, 1999 update The owner of an America Online account that apparently was used to inject the Melissa virus into the wild says he had nothing to do with it, and he is planning to close his account because of the online giant's "lack of security." "I am a little jarred about the lack of security that AOL has in place, and am now going to close my AOL account," (Name) said in an email. "We are aggressively looking into it," said AOL spokeswoman (Name). "There are a number of variables that need to be further investigated before we can make a determination about whether it was an unwitting propagation." Beyond that, she said AOL doesn't comment on individual users' accounts. The Melissa virus, which was introduced in "alt.sex" newsgroups early Friday morning, uses a combination of Microsoft's Outlook and Word programs to spread, taking advantage of users' email address book entries to gain the appearance of coming from a known person. The virus has the potential not only to spread to hundreds of users its original virus-infected document, "list.doc," but also future Word documents carrying Melissa after the initial infection. "I am not the creator of the virus, nor did I have any part in the distribution of the virus," (Name) said. Because of Melissa's notoriety, Steinmetz said his email traffic jumped from 2 messages per week to 20 per hour. Among the messages are hate mail, fan mail, requests from virus programmers for code, and requests from news organizations. The FBI is determining whether the virus meets the requirements in the criminal code for an investigation, FBI spokesman (Name) said today. The virus could violate laws that forbid "the transmission of a program, information, code, or command" that "intentionally causes damage, without authorization, to a protected computer," (Name) said. Antivirus software companies said one danger for Melissa damage was in overburdened email servers. However, AOL, which handles an average of 51 million messages per day, didn't see a significant increase in traffic, AOL's (Name) said.
In addition, a copycat of Melissa called "Papa" was first posted in the alt.bondage newsgroup, said Sal Viveros, group marketing manager at Network Associates. Papa virus, which affects Excel spreadsheets. Reports of a new strain surfaced yesterday when a similar virus called Papa, which is programmed to send out even more e-mails than Melissa, was discovered. The virus is attached to a Word document, so PC users have been advised not to open Word documents, not to allow Macros and to turn on Macro guards. While systems administrators are still trying to sort out the effect of the Melissa virus, a leading vendor of antivirus software has discovered a similar virus that could be even more dangerous. Network Associates late Monday said the new virus, nicknamed Papa, is an Excel virus that is transmitted in the same manner as Melissa. What's worse is instead of sending itself to the first 50 people in a Microsoft Outlook address book, the virus is sent to the first 60. Papa also sends an e-mail every time the virus is activated whereas Melissa only sends a message the first time it is opened. E-mails containing the Papa virus commonly contain the subject "all.net and Fred Cohen." The e-mail also contains an Excel attachment with the file name "path.xls." Once the attachment is opened, Microsoft Word will ask whether or not it should disable macros. Replying yes stops the e-mail from being sent to those listed in an Outlook address book. Network Associates said the worst thing about Papa is the fact it "pings" an undetermined external site to ensure an Internet connection is active. The virus pings the site so many times that it takes down the network. It also lowers the security settings on infected systems. Documents infected with the Papa virus are spread just as documents infected with Melissa. Network Associates virus experts believe Papa was not authored by the same person as Melissa, but they do believe it was patterned after the original virus. The fact that the two do share common traits is making it easier for antivirus software vendors to craft a way to detect and clean them. Network Associates is currently working on a fix for Papa and has already posted a fix for Melissa.. Systems most at risk are Microsoft Exchange servers running Microsoft Outlook. Systems administrators across the country were feeling the effects of Melissa Monday and the FBI confirmed its computer crimes unit was launching an investigation into the attack.
Melissa and Papa can only affect computers using Outlook, rather than Outlook Express, and the Word 97/2000 and Excel programs. Melissa virus goes global How Melissa Spreads
There are now two Mutants derived from Melissa
Mad Cow and Papab
Which so far known to act like Melissa
The major independent antivirus vendors now have "cures" for Melissa posted for download.

Melissa has gone World Wide
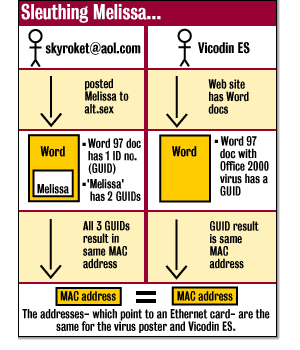
Melissa was first brought about
in alt.sex by someone useing skyrocket
the chalenge is that someone
utilized skyrocket's user name to bring about
Melissa by prduceing the List.zip
attachment
which was induced by way of
alt.sex into a users PC then to that users program then when the user loged
on to the WWW Melissa was brought about spreading and Mutating into our
Cyber World
Posted March 30th 1999